How the rapid increase in computing power and affordability of advanced technologies are driving the move from legacy analog EW systems to new digital ones.
A recent feature by Northrop Grumman provided some interesting insights into how the Electronic Warfare (EW) is moving away from the analog era and embracing the new digital technologies. Over the past decades, infrared countermeasures and analog EW systems were highly effective to protect aircrews against legacy anti-aircraft weapons during combat operations.
Nowadays, new generation threats are emerging all over the world, both in regard of anti-aircraft weapons (the so-called “double digit SAMs” like the SA-21/S400 and new air-to-air missiles) and new EW capabilities, all based on new digital technologies. As mentioned by NG in their feature, a digital battle for the electronic warfare domain is underway, with adversaries seeking to control the electromagnetic spectrum and deny access to airspace by using sophisticated and agile multi-spectral systems and creating dense, highly contested environments.
Electronic Warfare
The control of the electromagnetic spectrum is a major part of today’s warfare which, if neglected, can compromise the mission’s success. EW provides a vitally important function by protecting the access and use of the electromagnetic spectrum while simultaneously degrading or denying an adversary to do the same.
EW systems can be configured for a variety of missions, usually grouped in three main categories: Electronic Attack (EA), Electronic Protection (EP) and Electronic Support Measures (ESM).
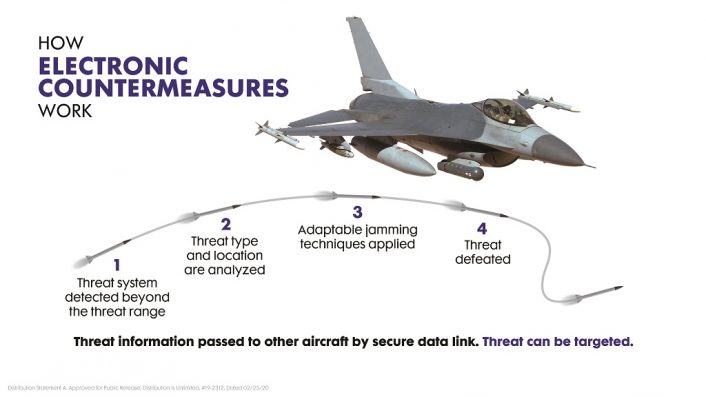
Electronic Attack is the offensive use of EW to degrade or deny an adversary’s use of the spectrum. Today EA is an integral part of military operations. Two of the better-known examples of EA are the Suppression of Enemy Air Defenses (SEAD) and offensive jamming used to disrupt communications.
Electronic protection is the defensive use of EW for individual aircraft, ships, ground vehicles and personnel from electronic threats. EP systems provide active protection to counter EA, by using means like expendable countermeasures (chaff, flares, towed decoys) and defensive jamming.
Electronic Support Measures provide situational awareness and understanding of the electromagnetic battlespace by creating an operational picture of allied and adversary positions. A tactical example is the Radar Warning Receiver (RWR), while more strategic ones are Signals Intelligence (SIGINT), Communications Intelligence (COMINT) and Electronic Intelligence (ELINT) assets used to create the Electronic Order of Battle (EOB).
ESM are tactically important because they allow prioritization of potential threats in real time for improved decision making. Because of this, they are often integrated with EA and EP systems, like the RWR coupled with expendable countermeasures and jammers for self-protection or the HTS pod (AN/ASQ-213 HARM Targeting System) coupled with AGM-88 HARM (High-speed Anti-Radiation Missile) missiles for SEAD/DEAD missions.
The three categories of EW systems we just mentioned have in turn three main common capabilities: sensing the environment, analyzing the environment and reacting to the environment. To better understand this concept, let’s look at how a basic EW engagement scenario unfolds between generic Blue Air and Red Air aircraft.
The Red Air aircraft is the attacker and it could be either launching a missile or performing EA against the opponent. The Blue Air aircraft is the defender and the receiver sensor of its RWR detects the threat. After performing the analysis of the collected signal, the system determines the best reaction to defeat the threat and deploys expendables countermeasures and jamming signals, known also as Electronic CounterMeasures (ECM).
While the former creates false targets by passively reflecting the electromagnetic energy, the latter actively radiate the energy to exploit the electromagnetic noise limit of the Red Air aircraft’s systems. The noise is generally any unwanted signal that disturbs the system and generally there is a certain quantity of noise that is tolerated and ignored by the computer.
The jammer will then transmit a high-power signal to create noise higher than the adversary’s limit, so the EA action is degraded or interrupted. The Red Air aircraft, however, can still react and resist the jamming if it is equipped with Electronic Counter-CounterMeasures (ECCM).
Technology evolution
Many strategists now see the electromagnetic spectrum as a major battle domain that needs to be managed and dominated. Here is how USAF Col. Dan Javorsek, a Defense Advanced Research Projects Agency (DARPA) Program Manager in the Strategic Technology Office, describes the need for the EW to evolve to the digital era: “Being able to maneuver in the electromagnetic spectrum is a fundamental tenant of all operations and has been for some time. You can’t imagine any modern nation having a program without some expertise in the electromagnetic spectrum. Communications and EW all fit in the same part of the spectrum and you need to be able to manipulate that space.
The transition to the digital world gives us a lot of new capabilities, but also a lot more things we need to manage. Most of the time there is an opportunity for the system user to modulate and control that, to use EW in an offensive and a defensive sense. If the user has maximum flexibility, which digital systems give us, that emphasis will move around a lot. The more we can control, manipulate and exploit the electromagnetic spectrum, the technology is really agnostic in terms of offense or defense.”
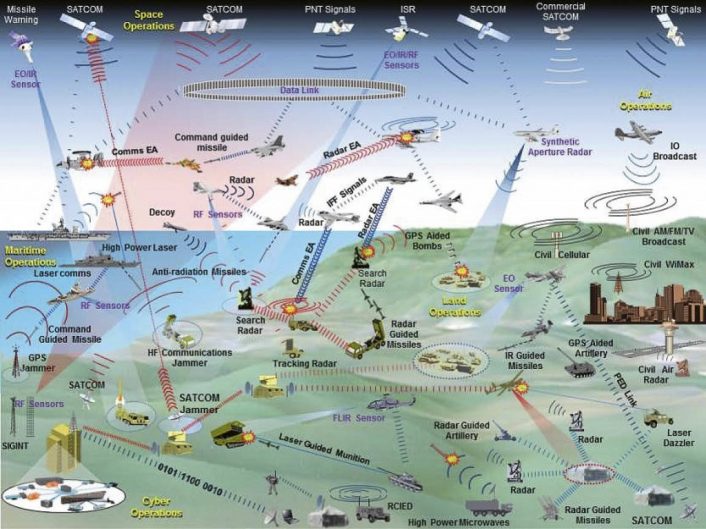
EW is a domain not visible to the human eye and until roughly 30 years ago it was not considered as interesting, being limited to just radars. With the evolution of technology, and especially the move to analog to digital, modern military systems begun to rely increasingly on the electromagnetic spectrum, using it to communicate, to gather intelligence about the combat environment, to accurately identify and engage targets, and for self-protection.
While decades ago advanced EW systems were the exclusive of wealthier nations, today’s evolution of technology and the affordability of commercial off-the-shelf electronics with increased computing power is leveling the field. For instance, some modern EW systems run on computers based on the Intel i7 Quad Core processors, the same that we can find in normal consumer computers.
A technology that contributed to this is the Microwave Monolithic Integrated Circuit (MMIC), which allowed the development of miniaturized RF (Radio Frequency) receivers that offer an increase of the capabilities compared to older systems. These receivers are accompanied by high-quality and high-speed broadband Analog-to-Digital Converters that overcome the signal’s quality degradation of analog receivers, and new interferometer antenna systems that now can determine the direction of a threat with an accuracy of 0.05 degrees instead of the one degree accuracy of older antennas.
Thanks to the new antennas and increased computing power, modern radars and EW systems are capable of simultaneously operating on more than one frequency band, shifting in real-time and covering a wider array of the electromagnetic spectrum.
Another concept that is making its way in the EW systems world is SWaP (Size, Weight, and Power) reduction. This, together with open systems architectures, is allowing cost-effective systems that are easily upgradable by replacing only some components, instead of the entire system, or even by just updating the software.
In turn, these new systems are easily reprogrammable to allow the best configuration for each mission, being able to switch in real time from one function to another and to integrate Artificial Intelligence and Machine Learning, paving the way for a new generation of cognitive and adaptive EW systems.
Digital EW
Northrop Grumman sums up the description of the new technologies and their advantages in these few sentences: “Fully digital and founded on secure, modular, open systems design principles, ultra-wideband digital receiver/exciter at its core provides significant advantages over heritage systems. This technology allows for extended frequency coverage, full spatial coverage and more rapid responses. Featuring highly efficient broadband power amplifiers and adaptive countermeasure modulations, it is designed to detect, identify, locate and defeat next generation sensors and weapons.”

Legacy systems worked efficiently for decades but are limited by their technologies. The new EW systems need to stay ahead of emerging threats while avoiding a quick and costly obsolescence that could be caused by the advancement in technologies.
Digital systems are the solution to the problem, as NG stated on its website: “Electronic warfare suites can now perform multiple functions and support diverse mission sets, and components and software can be shared among a family of systems. Under this building block approach, development costs and timelines decrease, upgrade cycles are faster and economies of scale kick in during production. As new threats are identified, enhancements can be shared quickly throughout the product line. Often, only a software change is required to add new capabilities, minimizing the obsolescence risk and decreasing the time to field.”
The obsolescence risk is even higher for the fourth generation fleet, whose systems are based on older technologies and need to stay relevant in current and future scenarios alongside fifth generation aircraft. The F-16 Fighting Falcon, for instance, is one of the most widespread aircraft of the 4th generation. NG is currently working on a new internal EW suite, based on a digital RWR and ultra-wideband architecture, to help keep the Viper effective for decades to come even in highly complex and contested electromagnetic spectrum environments.
For decades the F-16 relied on external pods like the ALQ-131 ECM pod, one of the most-installed electronic countermeasure systems ever, and now can use the station freed by the pod for another fuel tank, for example. The ALQ-131 is also being upgraded to offer the new EW suite of the F-16 in a podded solution for export, called ALQ-131C.

Another advantage of the new digital systems described here is the adoption of EW systems by a broader range of platforms, which now include cargo and air refueling aircraft, Unmanned Aircraft Systems (UAS) and intelligence assets, while until less than two decades ago EW systems were an exclusive of tactical aircraft. One example that we reported here at TheAviationist is the installation of internal Radio Frequency Countermeasure (RFCM) systems for the AC-130J Ghostrider and MC-130J Commando II.
Two of the most characteristic capabilities introduced with the advent of digital technologies in the EW world are adaptive EW and Digital Radio Frequency memory (DRFM) systems.
Adaptive EW uses machine learning to collect, analyze and implement reactions to RF threats. Currently, EW systems provide automated responses to threats which are known that are pre-programmed in their databases. Adaptive systems allow to negotiate even an unknown threat based on available information from the database or previous missions elaborated by the Artificial Intelligence in real time. This allows also to counter software-defined EW systems that can be changed on the fly and may be unknown by a database.
DRFM systems provide a more complex approach to EW protection by modifying the radar signal to create false targets. This involves the reception of a radar signal that is digitized processed and altered in real time, and then converted back to analog and retransmitted. The system has to avoid signal degradation and keep the altered signal coherent with the source of the original signal.
DRFM is highly effective in jammers, for an instance. Described in simple terms, the system digitizes the received signal and stores a coherent altered copy in digital memory, replicating and retransmitting it when needed. Since this is a coherent representation of the original signal, the adversary’s radar will not be able to distinguish it from other legitimate signals and will recognize it as a real target. DRFM can be used to create false range targets both behind (reactive jamming) and ahead of (predictive jamming) the asset that it’s protecting.
The “cyber evolution” of EW
The future will also see the convergence between RF and cyber-based EW: Electronic Attack aircraft are about to field technologies that will allow them to “hack” or inject malware into enemy networks.
This is what David Cenciotti wrote in a previous article on this topic:
In the past, U.S. Air Force EC-130H Compass Call aircraft have been involved in demos attacking networks from the air, a kind of mission that is far from new. In 2007, the success of Israeli Air Force’s Operation Orchard against a Syrian nuclear installation was largely attributed to effectiveness of the Israeli Electronic Warfare platforms that supported the air strike and made the Syrian radars blind: some sources believe that Operation Orchard saw the baptism of fire of the Suter airborne network system against Syrian radar systems. Although the details surrounding this capability are a bit fuzzy, the F-35 AESA radar could be able to do the same thing.
We have also reached out to NAVAIR to have an update on the EA-18G Growler’s Cyber Attack capabilities.
“Boeing is currently developing the Block II Growler, which will feature the Advanced Cockpit System of the Block III Super Hornet as well as improved sensors and upgraded electronic attack systems; however, those requirements are still in development, so we cannot provide further details at this time,” F/A-18 & EA-18G Program Office (PMA-265) explained us in an email.
Indeed, Boeing plans to improve the Growler’s electronic attack sensors and it is considering enhancements to Northrop Grumman’s ALQ-218 sensor system, which is used by the Growler for radar warning, electronic support measures and electronic intelligence, DefenseNews reported last year.
Although not officially confirmed, the Cyber Attack capabilities will probably be available in the future, with the Block II upgrade and the NGJ (Next Generation Jamming) pods.
The EA-18G is equipped with an airborne electronic attack (AEA) avionics suite that has evolved from the EA-6B’s Improved Capability III (ICAP III) AEA system. The EA-18G carries AN/ALQ-99 jamming pods, which are to be replaced by Next Generation Jammer jamming pods we have covered in detail in some recent articles.
The Navy states that “the EA-18G’s electronic attack upgrades meet or exceed EA-6B Airborne… Electronic Attack capability to detect, identify, locate and suppress hostile [electromagnetic] emitters; provide enhanced connectivity to National, Theater and strike assets; and provide organic precision emitter targeting for employment of onboard suppression weapons to fulfill operational requirements.”
In an article titled “A look at the US Navy’s Next Generation Jammer” published in 2018, dealing with the Cyber Warfare capabilities of the new pod, Dr Gareth Evans wrote:
The NGJ reportedly goes beyond traditional jamming too, adding signals intelligence and a communications hub capability to the more usual EW and radar tasks for the AESA array.
There have also been some reports that the system has the potential ability to launch a cyber-attack, involving inserting rogue data packets into enemy systems in a so-called “network invasion.” Such an attack is rumoured to have played a part in the 2007 Israeli ‘Operation Orchard’ raid on a nuclear plant near the eastern Syrian city of Dir A-Zur, in which BAE’s ‘Suter’ airborne network attack system was said to have shut down Syria’s Russian-made air defences.
The US Navy alluded to its interest in the idea in its 2015 ‘A Cooperative Strategy for 21st Century Seapower’, adding ‘all-domain access’ to the traditional four functions of the fleet, and according anti-access/area denial threats almost the same priority as nuclear deterrence. It would hardly come as a big surprise, then, if the reports of the new system’s additional cyber offensive capability were ultimately to turn out to be true.
Other articles, published even before 2018, mentioned the “Suter-esque” cyber attack capability to complement the EW attack capabilities of the Growler as well as its weapons giving U.S. military planners three SEAD options: jamming, bombing, and hacking.
Therefore, while the Cyber Attack is probably something coming with the NGJ pods, considered my background as a Computer Engineer specialized in Cyber Security, I’d be curious to understand a bit more about it:
is the Growler supposed to bridge the air gap and make the target network reachable even though it was supposed to be closed acting like a flying gateway? Or will the EA-18G dispense swarm of drones which, either autonomously or guided by a manned aircraft (in a loyal wingman scenario), will carry a malware designed to attack a specific target – a cyber weapon like the infamous Stuxnet, the virus that targeted the SCADA (Supervisory Control and Data Acquisition) control systems that manage pipelines, nuclear plants and various utility and manufacturing equipment – clse to the enemy network and systems?
Whatever, while we don’t know exactly when and to what extent the EA-18G will be able to launch a Cyber Attack or support it, it’s safe to say that the mere fact that this cyber capability is being developed (and probably, soon, implemented too) just confirms what we have been saying for quite some time: drones, AI (Artificial Intelligence), new cyber capabilities (and threats) are already changing the way air forces are preparing to fight future wars.









