Latest Information Security News
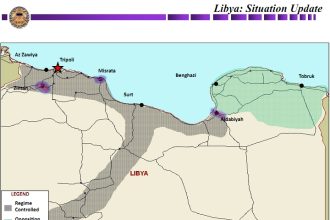
Operation Odyssey Dawn explained (Day 9)
Previous debriefings: Day 1 Day 2 Day 3 Day 4 Day 5…
Operation Odyssey Dawn explained (Day 6)
Previous debriefings: Day 1 Day 2 Day 3 Day 4 Day 5…
Targeting Iran's nuclear program with Stuxnet virus
I must confess that I hadn't heard about Stuxnet until my close…
Can malware cause an aviation disaster?
The answer is of course yes. Let's change the question: did a…
Is B747-8 hackable?
According to the Special Conditions issued by the FAA (Federal Aviation Administration)…
NFL technology for UAVs video analysis
American Football is one of my favourite sports and in these days…