See How USAF Aggressors Jam Civilian GPS Signals in Training at Nellis Air Force Base
GPS Jamming is a New Story from Red Flag 18-1, But We…
Israel Blamed for Fueling Flame Cyber Weapon in Middle East
The day after its discovery, there are few doubts that the infamous…
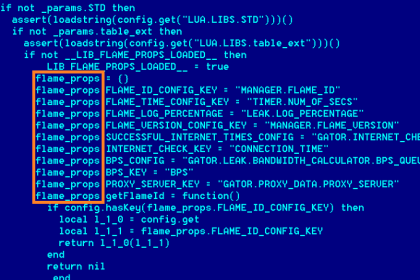
Flame malware infiltrating Middle East computers: the most complex Cyber Weapon, ever!
Irony of fate: not even a day after the publication of a…
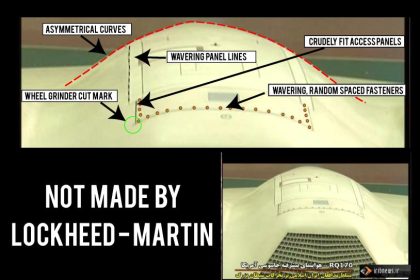
Middle East Cyber War: Revenge Of The Drones
In the same hours in which I was publishing my post on…
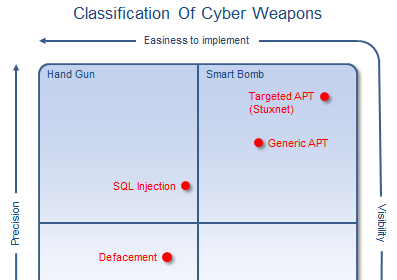
What is a Cyber Weapon?
We've been taking about Militarisation of cyberspace for some time now. This…
After latest F-35 hack, Lockheed Martin, BAe Systems, Elbit under multiple cyber attacks….right now.
I have just published a timeline covering the main Cyber Attacks targeting…