Aircraft and weapon types, launch times, and the estimated strike windows were all included in the latest screenshots released by Jeffrey Goldberg of The Atlantic, who was inadvertently added to a group chat of government officials.
In a follow up article to the initial bombshell report about The Atlantic editor-in-chief Jeffrey Goldberg’s inclusion in a group chat of top U.S. officials, we can now see specifically how the planned operation was described by U.S. Secretary of Defense Pete Hegseth.
Hegseth writes:
“TIME NOW (1144et): Weather is FAVORABLE. Just CONFIRMED w/CENTCOM we are a GO for mission launch.”
“1215et: F-18s LAUNCH (1st strike package)”
These F/A-18s (Hegseth used the designation F-18, which is not used officially) would have launched from the USS Harry S. Truman (CVN 75). Alongside these F/A-18s, which may have been a mix of single seat F/A-18E and twin seat F/A-18F Super Hornets, it is almost certain the carrier would have launched E-2D Hawkeye and EA-18G Growler aircraft to support the strike package.
CENTCOM Forces Launch Large Scale Operation Against Iran-Backed Houthis in Yemen
On March 15, U.S. Central Command initiated a series of operations consisting of precision strikes against Iran-backed Houthi targets across Yemen to defend American interests, deter enemies, and… pic.twitter.com/u5yx8WneoG
— U.S. Central Command (@CENTCOM) March 15, 2025
The Hawkeye would provide military and political commanders with a better picture of the battlespace as the operation unfolded, while also directing the strike package itself and increasing their situational awareness. With the AN/APS-145 radar of the Hawkeye active and scanning the airspace, there would be less need for the Super Hornets themselves to utilize their own radars and give away their positions.
EA-18G Growlers would monitor hostile radar emissions and, if necessary, neutralize any threat using electronic countermeasures or anti-radiation missiles. Land-based aircraft from U.S. bases across the Middle East would also have been available for support operations. As we detailed in reporting on Operation Neptune Spear, there are many layers involved in these military operations beyond the primary package itself.
“1345: ‘Trigger Based’ F-18 1st Strike Window Starts (Target Terrorist is @ his Known Location so SHOULD BE ON TIME – also, Strike Drones Launch (MQ-9s)”
‘Trigger based’ means this timing is subject to certain conditions being met. Most likely, given the section about the target’s present location, part of the trigger was the confirmation that the intended targeted individual was at the location they planned to strike. This means we know this specific strike package was targeted at an individual person and not equipment or operation locations.
Confirmation on the target’s location would require some degree of ongoing intelligence, surveillance, and reconnaissance (ISR) capability over the target. One of the most common platforms to use for persistent ISR in uncontested airspace is the MQ-9 Reaper, later mentioned as ‘strike drones’. An unarmed or lightly armed Reaper (allowing greater endurance) may have been providing ISR over the target prior to more heavily armed aircraft being launched.

It is also possible that more advanced ISR capabilities, be they aircraft-based or space-based, might have been used. Operations of stealthy unmanned aerial vehicles (UAVs) like the RQ-170 Sentinel or the unacknowledged ‘RQ-180’ are not discussed in the public realm, but based on previous leaks and also on prior U.S. operational practice we can assume these advanced capabilities are available in the region.
Whether these would be used in a lower threat airspace environment like Yemen, rather than for ISR missions against nation state level opponents, is unclear. However, as multiple MQ-9 Reapers have been shot down by Houthi forces they may have been deployed as a more survivable option.
Alternatively, the source of intelligence may have been via human intelligence, or HUMINT, through a source on the ground inside Yemen.
“1410: More F-18s LAUNCH (2nd strike package)
1415: Strike Drones on Target (THIS IS WHEN THE FIRST BOMBS WILL DEFINITELY DROP, pending earlier ‘Trigger Based’ targets)”
More F/A-18 Super Hornets now launch from the Truman. Armed MQ-9 Reapers reach their target points. The Reapers’ mission has no trigger requirements, so Hegseth clarifies that 1415 would be the first definite time for weapon launch. This is providing that the F/A-18s launched earlier had not already released their weapons.
Interestingly, this timeframe provides only 30 minutes for the MQ-9 Reapers assigned to carry out airstrikes to arrive on target after launch. While the aircraft are based nearby, including in Djibouti, the transit speed of an MQ-9 is not particularly fast. This may mean there is an MQ-9 operating location even closer to Yemen.
of all the hubbub over the signal groupchat has anyone noticed that the timeline between MQ-9 takeoff and MQ-9s striking targets inside Yemen is a half hour? and they take off *after* the much faster F-18s? this means a US drone base inside Saudi, correct?
— A-100 gecs (@PinstripeBungle) March 26, 2025
“1536 F-18 2nd Strike Starts – also, first sea-based Tomahawks launched.
MORE TO FOLLOW (per timeline)”
Truman’s second wave of aircraft will now begin striking their assigned targets while U.S. Navy vessels launch BGM-109 Tomahawk cruise missiles. Footage from the USS Gettysburg (CG 64), a Ticonderoga class guided missile cruiser, was released showing these missiles launching from the ship’s Mark 41 vertical launch system (VLS) silos. Other ships, such as the Arleigh Burke class destroyers that make up the bulk of the Truman’s escort may also have fired their missiles.
USS Gettysburg (CG 64) delivered lethal precision March 15 on Houthi targets in Yemen. America’s Navy is ready and fully committed to defending freedom of navigation around the world. #NavyReady pic.twitter.com/GNqPEaZgtj
— U.S. Navy (@USNavy) March 16, 2025
Current U.S. Navy VLS loadouts in this region will be a delicately weighted balance of offensive and defensive capabilities. In Tomahawk strikes during previous conflicts, we have seen ships launching salvos up to 30 missiles or perhaps more. Now, with the very real threat of attack by cruise and ballistic missiles, as well as attack drones, a greater requirement for anti-air missiles is clear.
“We are currently clean on OPSEC”
This reference to OPSEC, or operational security, is likely clarifying that the details of the mission has not been compromised in a way that would prohibit it from taking place. Obviously, at this point, the U.S. officials in the group chat were unaware of the presence of a civilian journalist.
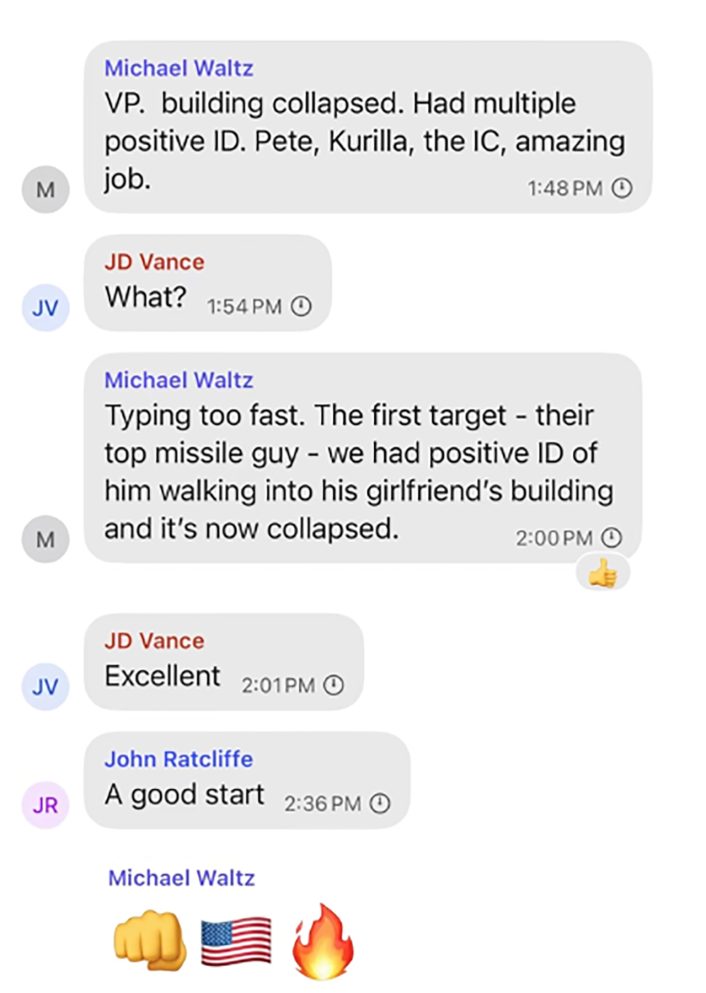
National Security Adviser Michael Waltz, a former special forces officer in the U.S. Army, then provided an update on the results of a portion of the strikes. He claimed they had a “positive ID” on their target walking into a building, and that the building had now “collapsed” as a result of the attack. In rough terms, providing the group chat with a battle damage assessment, or BDA.
Celebratory messages then arrived from U.S. Vice President JD Vance, Secretary of State Marco Rubio, White House Chief of Staff Susie Wiles, and others.
Unprecedented Leak
We have never before seen such recent direct communications between U.S. government officials regarding ongoing military operations, and perhaps we never will again. One reason why this is the case is that usually this information would be confined to a Sensitive Compartmentalized Information Facility or SCIF. These are secure spaces where classified materials can be handled and discussed. They may be a room inside a building, or even an entire building itself.
Personal devices, such as phones, tablets, laptops, are not permitted inside a SCIF. This means, in theory, there should be a permanent and physical air gap between any sensitive information and these devices.
It is clear to see why, therefore, much furore has erupted over the use of an app-based messaging service to discuss these plans. We do not know exactly what level of classification applied to this information in practice, but online commentary suggests it would likely warrant a SECRET or TOP SECRET marking.
As @BradMossEsq points out, this message from Walz reveals that the USG had real-time coverage of one of the targets at a very time. If this came from an IC asset, this would be classified at the SECRET or TOP SECRET level, per the ODNI classification guide. pic.twitter.com/ERf1ANGej8
— Secrets and Laws (@secretsandlaws) March 26, 2025
I’ve acted as a Red Team in war-games a few times, let me explain why this information release was dangerous. 1. The time over target allows an enemy air defences to set their watches for you 2. The launch time signposted the most vulnerable time slot to attack the Carrier Group. https://t.co/yxqUKE26Nq pic.twitter.com/e0Td0vdo5F
— Greg Bagwell (@gregbagwell) March 26, 2025
Signal is a messaging service with tens of millions of monthly users. While it was already known that the app is used extensively by politicians and those who work with them, in this use it should primarily be used for non-sensitive communications.
The AES-256 encryption used to provide end to end encryption for the messaging service is sufficient for the transmission of TOP SECRET level information, according to the U.S. government, but this does not protect information from hacking attacks against a user’s device itself. Should one individual’s device be compromised, whoever has compromised the phone can in theory access their messages and any of the group chats they are in.
Top level politicians and officials are, of course, prime targets for foreign intelligence agencies who spend large amounts of time and money devising ways to infiltrate these devices.
We do not know whether this is the first time Signal has been used for such communications, as the only reason this instance has become public knowledge is through the inclusion of Goldberg in the chat. Prior to this story, the U.S. Department of Defense (DoD) issued a warning to its staff that Russian intelligence agencies had been exploiting Signal’s linked device feature to compromise messages.
The Pentagon Sent Out a Warning Against Using Signal Right Before Yemen Group Chat Fiasco https://t.co/5R5D99CgBB
— Gizmodo (@Gizmodo) March 25, 2025
The initial reports were discussed before the Senate Intelligence Committee on Mar. 25. Calls for a full, independent investigation into the leaks have come from both Democrat and Republican politicians, as well as many in the fields of defense, security, and intelligence. Multiple members of Congress have additionally called for Hegseth and Waltz, the two members of the chat who posted the intricate details of the operation, to resign.








