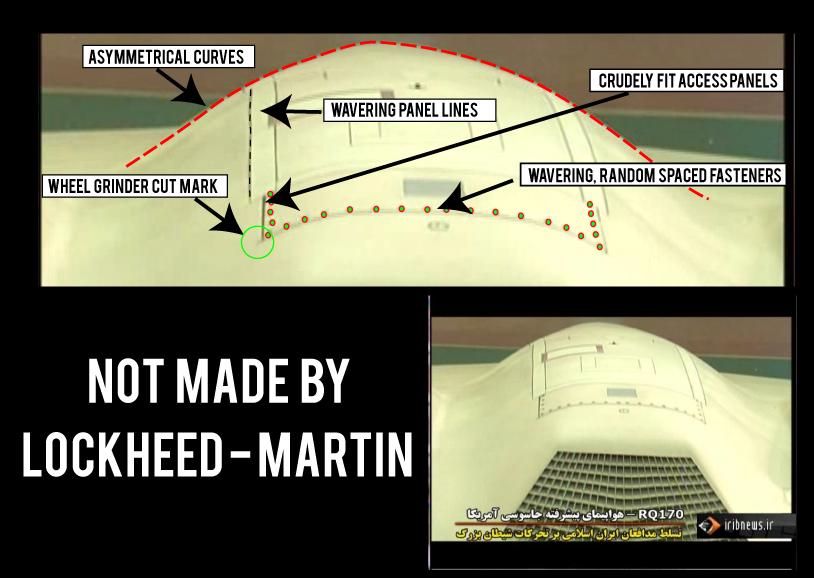
Let’s Talk About The Secretive RQ-170 Sentinel Photographed In Flight Over California Desert Recently
The drone, apparently in a test configuration, was spotted over the desert south of Edwards Air Force Base. The secretive RQ-170 Sentinel low-observable Unmanned Aerial Vehicle, also known as the “Beast of Kandahar” (from where […]