New ODIN Hardware Destined To Host F-35’s ALIS Replacement Successfully Tested At MCAS Yuma
The F-35 Lightning II Joint Program Office, in partnership with Lockheed Martin,…
What Do New Technologies And Digital Transformation Mean To The Military?
New Technologies, IoT And Cyber Threats Are Changing The Way War Is…
A Cyber attack by Syrian Electronic Army may be Assad’s most dangerous reaction to U.S. air strikes
Considered the current status of the Syrian military, whose capabilities have been…
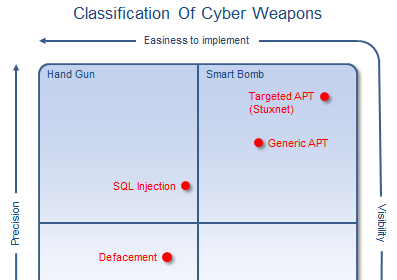
What is a Cyber Weapon?
We've been taking about Militarisation of cyberspace for some time now. This…
After latest F-35 hack, Lockheed Martin, BAe Systems, Elbit under multiple cyber attacks….right now.
I have just published a timeline covering the main Cyber Attacks targeting…
Exclusive Infographic: all Cyber Attacks on Military Aviation and Aerospace Industry
2011 has been an annus horribilis for information security, and aviation has…